Rocky Mountain Technical Marketing, Inc. | Supply-Chain Integrity
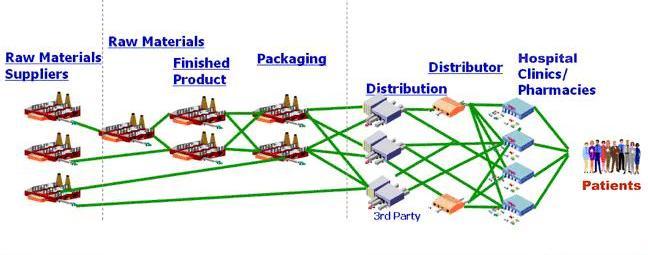
Advances in technology, combined with globalization, have facilitated counterfeiting on an unprecedented scale. This practice not only diverts revenue from makers of brand name products, but in industries such as pharmaceuticals, counterfeit and diluted products put the general public at risk. According to Interpol more than one million people die each year from counterfeit drugs!
Rocky Mountain Technical Marketing, Inc. (RMTM) has developed a supply-chain integrity solution that leverages proven encryption technology to create a robust chain-of-custody transaction log that cannot be repudiated.
RMTM’s solution not only tracks the chain of custody for goods throughout the supply chain (which can include all transporters), it also tracks the quantities of product transferred at each change of custody. The solution ensures that the quantity in circulation never exceeds the quantity produced. This removes the incentive to sell counterfeit goods. If a distributor received 300 items, it can only sell 300 items without triggering an alert. And the solution prevents gray-marketers from validating the authenticity of their products.
The solution is designed to work with sensors for important parameters such as temperature and humidity to identify goods that have become spoiled or compromised.
Equally important in many industries, the details of each transaction are stored in an encrypted form that restricts the dissemination of information in the chain-of-custody log on a need-to-know basis. The rules for “need-to-know” are customized to meet the unique requirements of each industry using the solution.
For example, if a drug required recall, the manufacturer could input a notice to the system and the system would disseminate the notice to all downstream members of the supply chain without exposing the customer information of downstream distributors to the manufacturer.
Furthermore, the encrypted log is stored in a distributed database to make it resistant to hacking. The single source of truth is determined by a preponderance of identical records stored in the distributed database.
Our solution supports existing RFID, bar code readers, and other rapid-scan equipment at each transfer point to provide integrity protection at minimal cost. It can support identification standards such as those from GS1 and can support the unique information requirements of national and regional regulators, such as serialization and global track and trace.
RMTM tailors our supply-chain integrity solution to each customer’s supply chain. It can also be used across an industry (e.g., pharmaceuticals or electronics) to allow a single solution to support the complex product web.
With specific regard to the pharmaceutical supply chain and compliance with the US Drug Supply Chain Security Act, see the following:
A Solution for Pharmaceutical Track and Trace in the United States – Part 1
A Solution for Pharmaceutical Track and Trace in the United States – Part 2
