By Jeff Stollman, principal consultant, RMTMinc.com
After spending several years working in the blockchain ecosystem, I am continuously amazed at how much energy we waste talking past one another because we lack a common understanding of the terms that we use. Much vitriol is expended in debates in which parties may be in furious agreement, but are so lost in their own personal definitions of terms that they don’t recognize their agreement. Still others hold zealously to certain opinions that cannot be supported if they took the time to define their terms. Instead, they use broad terms such as “decentralization” in multiple ways during the same conversation, dancing between the definitions as it suits them to make their points, never realizing that they are talking in circles.
In an effort to save us from ourselves, I believe that there is a need to develop a common set of definitions. These will allow us to continue moving forward, rather than continuous chasing our tails. What I propose below is a straw man. I don’t claim that these definitions are “right” by some divine power invested in me. (I haven’t known it all since I was 17. And that was half a century ago.) I welcome feedback from others who would prefer their own definitions. In the end, the community, as a whole, will decide. But if we don’t start the conversation now, we will continue to lose time and energy in fruitless controversy.
Bitcoin
1. An application that generates and tracks the movement of its namesake cryptocurrency. Bitcoin employs a variety of techniques and technologies to propagate its ecosystem. These include
1. Blockchain technology to make the log of Bitcoin transactions tamper evident
2. Proof of Work (PoW) to incentivize participation in a consensus mechanism to validate new transactions.
3. Block Creation that bundles transactions into groups that can be validated together to increase throughput
4. Mining is an incentive program built into Bitcoin that creates new cryptocurrency tokens and disseminates them to those who participate in the PoW validation process. The incentive system served to bootstrap Bitcoin. The offer of financial incentives served to broaden interest and participation in validating transactions. Increased participation in validation serves to increase the integrity of the Bitcoin application. It also served to increase interest and participation in using the Bitcoin application generally. Only 20 million Bitcoins have been set aside for mining. Mining rewards will terminate once these have been awarded to validators. At that point, validators may substitute transaction fees to justify their investment of time and equipment in the ongoing validation of new transactions.
5. Distributed copies of the Bitcoin transaction log to
1. Provide business continuity resilience should one or more nodes lose connectivity to the network
2. Enhance tamper resistance by creating more copies of the log that need to be consistently altered to falsify existing records
3. A second consensus mechanism to compare copies of the transaction log in order to discover and repair versions that are out of sync with the majority of copies.
Blockchain
1. A cryptographically linked list in which each new record contains a cryptographic hash of its predecessor and is “signed” (i.e., its own has begins with a particular numeric sequence such as 0000). In this way, if a record is corrupted, its hash will change and all succeeding records will evidence this inconsistency because their hashes will no longer begin with the designated numeric sequence.
2. The explanation of blockchain given in the Bitcoin whitepaper is: “A timestamp server works by taking a hash of a block of items to be timestamped and widely publishing the hash, such as in a newspaper or Usenet post. The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it.”
3. A second cryptographic technology which can also provide tamper evidence similar to that provided by blockchain is called Directed Acyclic Graph (DAG). DAG solutions are technically not blockchains, but because they provide the same ability to rapidly show that a record has been tampered with, they are often implied in references to “blockchain.” Think of blockchain as a pliers and DAG as a wrench. Each tools works differently, but both can be used to unscrew a bolt.
Decentralization
1. A vague, generally undefined term, that people associate with blockchain solutions. In fact, the term can be decomposed into several different features including the following:
Architectural Decentralization
1. The redundancy of the architecture of a data system that provides it with the resiliency to continue operations if at least one node containing at least some of the data becomes inoperable or compromised.
Data Decentralization
1. The requirement that there be more than one nodes to represent the full content of a blockchain. If there are many nodes, but each node contains a complete copy of the data, the data is not decentralized.
Procedural Decentralization
1. The requirement that more than one independent validator is required to validate new transactions added to the system
Political Decentralization
1. The requirement that power to make and change rules for the system (governance) be distributed among the independent stakeholders of the system
2. Contrary to popular misconception, the various forms of decentralization described above are techniques to achieve certain goals. They are not a goals in themselves. To pursue decentralization for its own sake, unnecessarily constrains potential solutions.
Directed Acyclic Graph (DAG)
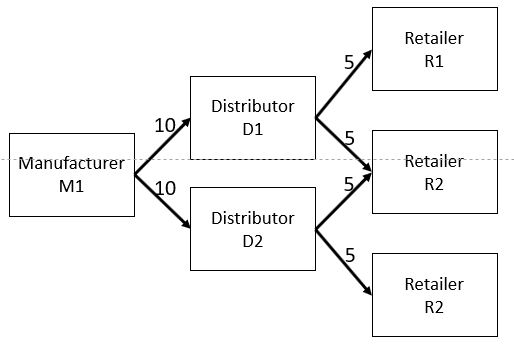
1. DAG is a mapping technique. When applied to transaction recording systems, it can map transactions that occur in only one direction. For example, Manufacturer M1 ships 10 widgets each to Distributors D1 and D2. Then Distributor D1 ships 5 widgets each to Retailer R1 and Retailer R2. Distributor D2 ships 5 widgets each of Retailer R2 and R3. A graph of this would look something like this:
2. The graph above is directed: it moves from left to right only. And it is acyclic: it does not not cycle back on itself. This particular DAG is a special case. It can be recorded in a single blockchain transaction record as a sequential list.
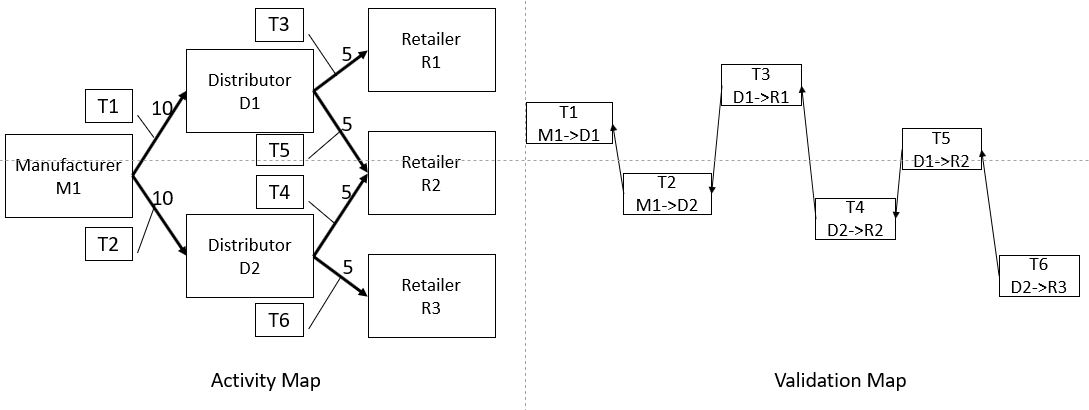
3. Blockchains typically use a validation technique the requires each new block to be validated based on the preceding block. Assuming for simplicity that each transaction is its own block, validation in a blockchain would look like the illustration below:
4. As seen in the illustration the validation of Transaction T2 is based on the preceding block Transaction T1. Similarly, T3 is based on T2, etc.
5. Solutions that tout themselves as DAGs typically validate the transaction based on the concurrence of the transacting parties. They do not require third-party validator. This eliminates the cost of mining. It also allows transactions to be validated in parallel, rather than in serial. This gives them greater throughput — a shortcoming of many of today’s blockchain solutions. A validation mapping illustration for a simple DAG is shown below.
6. This approach does present the potential for “double spend.” That is, in the supply chain graphic above, there needs to be a way to keep Distributor D1 from shipping 5 units each to Retailers R1, R2, and R3 (a total of 15 units), when he has received only 10 units from Manufacturer M1. Different DAG solutions resolve this problem in different ways.
Disintermediate
1. Removing intermediaries from a process.
2. Disintermediation is viewed by many as a goal of blockchain. It is a false goal. Blockchain does not remove intermediaries, it substitutes them. By using Bitcoin for payment, banks can be bypassed. Their role as a trusted intermediary is replaced by the Bitcoin blockchain. Transacting using Bitcoin (or other cryptocurrencies) still includes intermediary transaction fees, just as banks do. Bitcoin transaction fees may be lower than those currently offered by banks, but that is merely because it offers competition. In addition, because the entire world does not accept Bitcoin for payment, those transacting in Bitcoin also incur fees from exchanges to convert fiat currencies into Bitcoin to make the payment transactions. And the payee pays a similar fee to convert Bitcoin back to fiat currencies useful for its own expenses.
Distributed Ledger Technology
1. This is a popular term that has no clear definition. Some people use it as a synonym for “blockchain.” Others use it explicitly to distinguish an implementation from being a blockchain. Perhaps this is just a marketing statement: solution providers want to distance themselves from the hype around the term “blockchain” in order to be taken more seriously. But I have witnessed many people getting quite heated in debating whether a solution a blockchain or distributed ledger technology as if there is a clear and obvious distinction.
2. On its face, the term suggest that a ledger is used. This is a common feature of a blockchain solution, because a blockchain transaction record is a ledger of all of the transactions. Arguably, a Directed Acyclic Graph may also be a ledger. While a DAG may not be a single serial listing of the transactions, it does still record them all.
3. A second feature of the term is that it is distributed. This suggests that either complete copies of the ledger are stored in multiple locations or that pieces of the ledger are stored in multiple places. There is no clear consensus on this, but most solutions that call themselves distributed ledgers technology store full copies of the ledger in multiple locations. As I have noted in my definition of “blockchain”, even though most current blockchains do store their ledgers in multiple locations, this is not a mandatory requirement for creating a cryptographically linked list. Rather it is a preferred embodiment of many solutions that use blockchain’s cryptographically linked list.
Governance
1. The collection of rules that determine how a community operates.
2. These rules can include
– Who gets to participate in the community
– What rights each party has
– What rights each party has in any decision-making process including both the development of the initial rules and any subsequent modifications to them.
– How decision (voting) power is apportioned among stakeholders. (E.g., is voting power apportioned by one-party-one-vote, by transaction volume, hashing power, some combination, etc.)
Hash
1. A cryptographic technique that creates a unique one-way transformation of data. Any data can be hashed (text, graphics, audio, video). And the same data will always yield the same hash. Hashes typically have a fixed length (e.g., 256 or 512 characters). While it is extremely difficult to reverse a hashing function and reproduce the original from the hash, hashes are an effective way to ensure the authenticity of data. For example, if two copies of a document have the same hash they can be assumed to be identical. If even one character is off, they will have substantially different hashes.
Hashing power
1. A measure of the computing power of a device or group of devices for solving hash-related problems used in certain transaction validation techniques. To achieve procedural decentralization, it is important that hashing power be distributed among independent participants. The distribution of hashing power is more relevant than the distribution of participants because one participant (such as a mining pool) may be running enough devices to take over the network even if there are hundreds of smaller participants engaged in validation.
Independent
1. Non-colluding. Independence refers to the distinct motivation of each party. Independent parties operate without collusion. They may have the same values and motivations, but operate for their own account.
2. Merely having a large number of participants does not matter if they are not independent. While Bitcoin (and other “blockchain” applications, as well) may have many miners participating in its consensus mechanisms (thousands in the case of Bitcoin), many have aligned with mining collectives that operate as one. As few as three of these pools have the power to conduct a 51% attack on the system.
Intermediary
1. An entity that provides trust among parties transacting on a network. (The term network does not refer to the connectivity that facilitates the interactions. e., it is not the “network” layer – Layer 3 — in the classic Open Systems Interconnect stack.)
2. An intermediary may be
1. the owner of the network (e.g., a corporation such as Amazon or eBay or a non-profit foundation)
2. an independent party (e.g., an accounting firm that verifies a corporation’s financial reports to its shareholders
3. stakeholders in the network (e.g., miners on the Bitcoin or Ethereum network)
3. As per item 2.3 above, a blockchain, itself, can serve as an intermediary.
Node
1. A computing device that stores all or part of the transaction data in a system.
2. Depending on the particular technology underlying the application, nodes may also participate in the validation of new transactions and/or maintaining the consensus version of the already recorded transactions.
Smart Contract
1. A computer program stored on a blockchain that executes rules that follow the pattern IF->THEN,ELSE.
1. For example, the program may represent an agreement between Alice and Bob such that IF Alice sends Bob a widget, THEN $5 will be transferred from Bob’s account to Alice’s account, ELSE no funds transfer will take place.
2. Though the word “contract” is included in the term, it may not be a legally binding agreement.
3. It’s usefulness comes from the fact that the events are firmly enforced by the computer code. There is no wiggle room.
1. In the example transaction above, the smart contract could also require that Bob place $5 in escrow to ensure that as soon as Alice verifies shipment (or receipt is verified by Bob, perhaps through his signature on a shippers tablet) the funds are transferred.
4. Because the smart contract is stored on the blockchain, any tampering with the computer code can be promptly detected.
1. But writing smart contracts that are “bulletproof” is difficult. Millions of dollars have been stolen by exploiting flaws in smart-contract computer code. These thefts do not require modification of the code, merely exploitation of their flaws. Translating human intention into code can be challenging, depending on the complexity of the terms being encoded.
51% Attack
1. The validation protocols used for most blockchain (and DAG) solutions are vulnerable to a 51% attack. These means that if 51% of the participants (as measured by their hashing power) collude, they can take control of the system and create false records and/or modify past records.
2. Successful 51% attacks have already been conducted on some smaller blockchain networks.
3. Larger networks are also vulnerable when large numbers of validators band together into mining pools, reducing the number of independent validators.